The power of two: Appmore and SSH unites!
Experience the Unified Strength of Identity-Based Authentication, Privileged Access Management, and Workflow Approvals. By merging IAM and PAM, we provide an all-encompassing strategy for overseeing identities, authorizations, roles, and approval processes, all while maintaining vigilant monitoring and auditing. This ensures seamless operations and compliance with regulatory standards.
By merging IAM and PAM, we tap into their synergistic potential in the battle against advanced cyber threats. In collaboration with SSH, we’ve built a formidable platform that seamlessly integrates:
- IAM’s powerful identity and access governance (MFA, SSO, etc.) and entitlements
- PAM’s RBAC, access surveillance, session recording, and auditing
- Ticketing and approval workflows with seamless ServiceNow integration
How does it work?
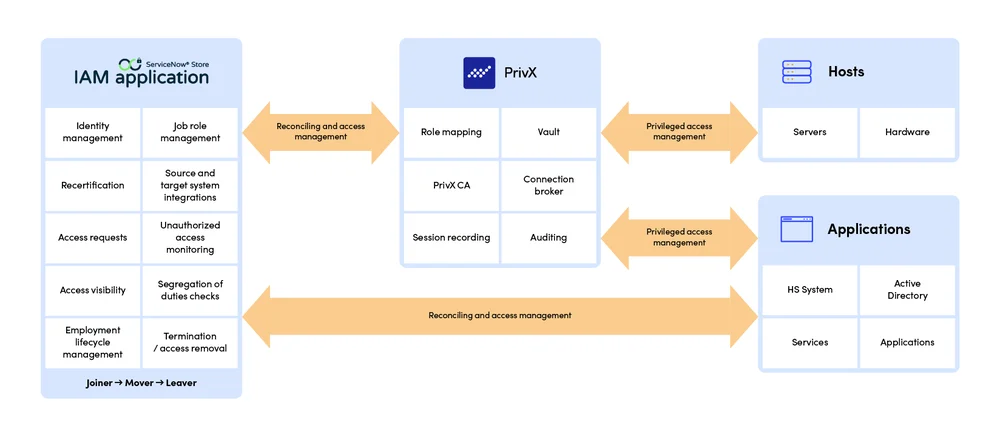
Access Management: Users request access via Appmore’s ServiceNow application, and admins grant access based on predefined roles. This integration streamlines access requests, eliminating the need for outdated methods. HR processes are seamlessly integrated with identity and privileged access management.
Passwordless Authentication: Users can opt for passwordless authentication, such as biometric methods. For situations requiring traditional credentials, like passwords and keys, they can still be securely managed, rotated, and stored.
Compliance and Monitoring: The solution equips organizations to meet access requirements under regulations like GDPR, ISO27K1, and PCI DSS. Access is automatically revoked in case of anomalies, ensuring compliance.
Automated Access Termination: Upon an employee’s departure, the IAM application deactivates user accounts and revokes all access privileges. Thanks to synchronization between PAM and IAM, access rights are terminated simultaneously. All activities, including requests, additions, grants, and removals, are meticulously tracked and logged.
