Information security plays an important role in both small and large companies. The corona pandemic has contributed to the fact that companies have begun to pay more attention to information security, as well as work efficiency and job satisfaction. The growth of remote working has brought extra challenges to access and information security management. For example, investments in physical security no longer protect systems in the same manner. Now you must trust that the processes, information security know-how and practices of employees as well as the security of the systems are at a sufficient level and there are no unnecessary access rights in the systems.
Identity and Access Management (IAM) is for ensuring that the right people in a corporation have the appropriate access to resources for the right reasons. Terms IAM and IGA (Identity Governance and Administration) are often used as synonyms even though IGA is a superset of IAM. Identity and Access Management is the process and tools for managing individuals’ identities and related accounts.
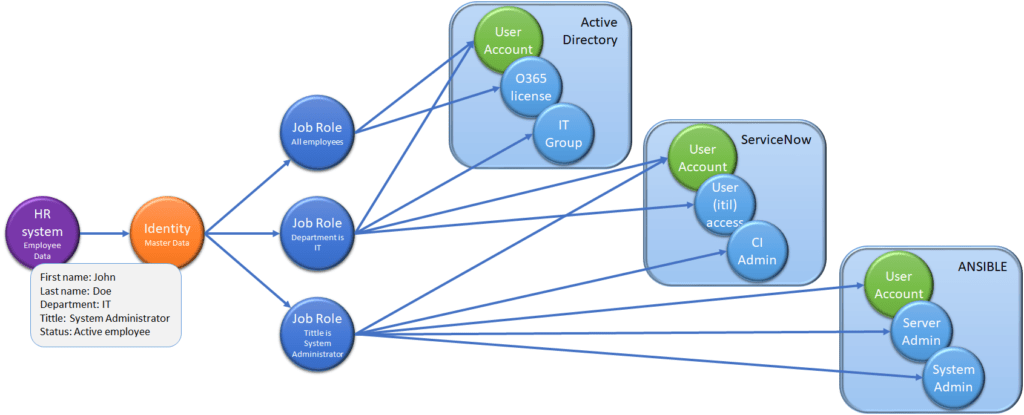
A person’s identity is conjunctive information for one specific person, and this involves information such as first name, last name, email address, etc. In addition to identity, information is needed about which systems a person can log in to, for what reasons and when. In addition to that user has separate accounts (user IDs) in each system, one user can also have several accounts in one system. For example, a person may have a normal user account as well as an administrative account. In addition to these, you also need to know what a person should and should not be able to do in the system. Management of these is usually based on roles, accesses, groups, and licenses.
Job roles are among the base processes in IAM. Job roles are combinations of accounts and access rights to different systems that can be granted based on a person’s identity. Attributes like department, position, or job title in an “identity card” can be used for assigning job roles. One person can have several job roles, and it must also be possible to order these separately.
IAM mitigates centralized identity and access management
For security reasons, companies should be able to manage the overall information of systems in some way. The information should be at least which systems a person has access to and what kind of accounts and access rights he or she has. With a well-built IAM system, you can see all the information from the same place, and you don’t have to dig the information from each system separately. IAM systems provide tools for running various reports for internal and external audits as well as any other security-related needs.
As an example, in a company with 200 different systems, it’s almost impossible to start going through the systems one by one removing rights when an employee leaves the company. Without IAM, there is a real security risk that the person will be left with rights to some system. In this case, it might be possible for the person to do considerable harm to the business in multiple ways. As an example, if the person was left with access to a register with Personally Identifiable Information (PII), the data could be used for blackmailing or just published on the internet. This would be a major security breach and might cause sanctions under GDPR for the company.
Examples of IAM use cases
A new employee is hired
A new employee is hired, and he or she must get access to 20 systems. In an organization that doesn’t have IAM in use, the process might go as follows. 1) Supervisors request access rights to the new employee via email or tickets. 2) The request goes to the Helpdesk. 3) Helpdesk will review the request and possibly ask for some approval. 4) The ticket waits until approval comes. 5) The ticket is back in the process and it is checked that the new employee is authorized to get access rights to different systems. 6.) Helpdesk adds access rights to each system manually.
A well-implemented IAM system enables the following process. A job role is created once the necessary access rights for different systems are identified for a certain position in an organization. The job role describes what kind of credentials a person requires in different systems and what rights should be given to a person in these systems, and the job role is linked to identity information.
In practice, Human Resources (HR) is the first contact point for a new employee. HR adds a new person into their system. The information from the HR system goes to the IAM (the information is either retrieved from the HR system or the HR system pushes the information to IAM) that the person X is about to start work after two weeks. The IAM system can now automatically check, that the person starts in department X and department-specific and all other matched job roles can be assigned to the person. When the person starts the first day at work, the whole process has already been handled automatically, and the Helpdesk didn’t need to assign access rights manually. For example, the person can log on to a laptop and have all the rights described in job roles associated to him or her. This brings cost savings to the company in terms of reduced workload and by mitigating human errors in adding access rights to the person. The automated processes also increase work efficiency and job satisfaction.
Security-Audit
Almost every company has both internal and external security audits as well as related recertifications of access rights. Access rights to the systems among other things are checked in security audits. In the worst-case scenario, this can be a time-consuming Excel exercise of retrieving information manually from each system separately and aggregating it on a personal level. Information about former employees might be found at this point and the access rights need to be removed immediately to avoid upcoming security risks.
In IAM, all information is in one place and in one format, making it is easy to check what kind of rights are assigned in different systems in real-time. When one identity binds all these together, it is easy to see that person X has access to these systems with these rights and X number of different accounts in these places. Based on this, recertification tasks can also be periodically created for the supervisors, who must check the rights of their employees by a certain date and sign these tasks as completed.
IAM is suitable for companies of almost any size
Depending on the industry even a company of 10 people may have 20 systems, in which case IAM may be necessary. IAM pricing is often user-based, so the cost may not be as high. If the company wants to invest in information security or wants to be for example ISO certified, it is recommended to have an IAM. Customer requirements and contracts may also require the company have some specific management for identities and access.
As a rule of thumb, the bigger the company the more difficult it is to manage identity and access without the right tools. Controlling the access rights of personnel can be very challenging and having many systems might cause bigger security risks. If IAM is deployed at an early stage, IAM can be added as part of the system acquisition and deployment process making access control management part of IAM from the beginning.
Benefits of IAM application
With an IAM application, a company can save a significant amount of resources that can be utilized for more productive work. Companies may also end up paying for unnecessary licenses if unnecessary access rights or accounts have not been inactivated from the systems. This can happen when a person is no longer an employee or when a tool is no longer needed due to some other circumstances.
Examples of the benefits of IAM:
- Cost savings from unused licenses
- Improved security
- Cost savings in managing accounts and access rights
- More committed and efficient employees
- Access to the systems within minutes after requesting access
- Automation reduces manual work and mitigates the possibility of human error
- Identities and access rights at the right time for the right reasons
- Cost savings in training and maintenance
Especially in larger companies, the savings on annual basis are significant both financially and in resources.
Implementation of IAM
Initial implementation of IAM can be a rather straightforward and lightweight process. You don’t have to and may not even be able to do everything at once. However, the number, complexity and diversity of the systems and the organization need to be taken into account to understand and master IAM as a whole. This might result in a large overall project of implementing IAM. The first phase of implementing IAM might take a couple of months introducing the basic features of IAM, HR integration and Active Directory integrations (be it Azure, on-Prem AD or Hybrid model). This would allow the company to assign access rights through job roles, request additional access rights via a portal, manage approvals, manage licenses, run audits/recertifications, monitor segregation of duties, run reports and give visibility for identities, accounts and access rights for appropriate users e.g. managers.
The basis of IAM is that it holds accurate and up-to-date information about the accounts and access rights to the systems, this process is known as reconciliation. In reconciliation information about different accounts and access rights in target systems are retrieved and synced with the IAM system. If someone has for example changed access rights without using the approved process, this will be noticed, and an Access Violation event can be raised. Access violation events can be configured to trigger automated removal of illegal rights in question, start an approval cycle or just report the violations as deviation. In addition, IAM can also control segregation of duties and Critical Access Combinations, preventing, for example, the same person from accepting and paying bills on behalf of the company, which would facilitate possible embezzlement. Any deviations can also be reported to the risk management system if one is used.
It is good to remember that IAM is a continuous process. For example, companies are buying new systems, organizations and systems are changing, and companies may merge which means that the IAM process should also constantly be updated and evolve to the new situations. Job roles should also be controlled and updated to meet new requirements. IAM should also be part of the implementation project for the new system, and automation (integrations) should be considered for both new and old systems.
Is IAM suitable for all systems?
IAM can be used with any system that has any kind of application interface allowing integration (API). If necessary, the system database can also be accessed directly, although this is not the preferred option. Applying software robotics (RPA) might be a viable option as well because not all systems, especially the older ones have a usable API. In this case, the system privileges are granted using predefined workflows and the robots handle the configuration as a normal user would.
IAM systems also support manual task-based management because it doesn’t always make sense to implement automation with every system. In practice, this means that all access rights and accounts are ordered from IAM according to the process in the same manner as for automated systems. The workflows of application and approval processes are similar to a fully integrated system, but some or all tasks need to be done manually and marked complete in IAM.
The process is easier than before because end users can order all access rights the same way using the same kind of forms, approvals are handled automatically based on rules, the application shows only the necessary information about the employee which can be copy-pasted to the target system, temporary passwords are automatically generated so new users will have unique temporary passwords and system will automatically inform end-users with instructions and temporary passwords. In addition to this, IAM provides up-to-date audit information like who ordered, who approved and timestamps of actions on any given change.
Even for manual systems, it is always a good idea to bring reconciliation information to IAM. If the integration cannot be built, then the accounts and rights can be imported into IAM even as Excel spreadsheets at certain intervals. Any system where accounts and access rights need to be managed is a worthy candidate to be put under IAM to mitigate the security risk.
Tips for starting an IAM project
The company can start to consider the IAM project by evaluating the risks, i.e., what kind of risks does the company have if for example, a former employee has access to the company’s systems, or what if someone has access to information that he or she should no longer have access to, or whether the company has agreements with customers where information should be protected differently, or if access rights should be managed better.
A company may also feel that it needs to be able to provide required access rights faster or better job satisfaction as well as efficiency in its operations. There may also be situations in companies where resources run out and new people are not allowed to be hired. Thus, the company can consider its needs through automation, cost savings and minimization of administrative costs.
The issue can also be considered from the perspective of the GDPR. The company must be able to demonstrate, that they have adequate security for the processing of personal data. At the same time, when looking at a company’s systems from a security perspective, more efficient ways to manage processes or even cost savings may be found.
The first step of an IAM project is to be aware of the potential risks and needs in the organization. The next step should be considering whether there is enough internal expertise to take the project forward or if external consultation is needed. The organization can then begin to map out the technology that suits their needs.
If your company has not yet invested in IAM, I recommend that you consider whether it would be the right time before it is too late.